Malware stands for “malicious software.” It’s any program or code designed to harm a computer system, website, or network. It can steal data, slow down performance, or even hijack your website for its own purposes.
The effects of a malware attack on your website can vary depending on different factors, like how quickly you respond to it. If you take too long to detect and remove the malware, it can end up costing more to recover from the attack. Certain types of malicious software are created to remain undetected, but over time, obvious indications of infection will begin to appear.
Signs of a Malware Attack:
Detecting malware on your website early can save you from significant damage and potential data loss. Here are key signs that indicate a malware attack:

Unexpected Website Behavior:
If your website starts behaving strangely, such as redirecting visitors to other sites, displaying unsolicited ads, or pop-ups that weren’t part of your original design, it’s a clear sign of malware.
Sudden Drop in Traffic:
If your website experiences a sudden drop in visitors, it could be a sign that it has been infected with malware. This happens because search engines recognize that your site is dangerous and block it, in order to keep people safe from potential harm. As a result, fewer people will visit your site.
Slow Loading Speeds:
Malware can significantly slow down your site’s performance because it uses the website’s resources to execute malicious tasks, which in return affects user experience negatively.
Google Blacklist Warning:
If Google has detected malware on your site, it will display a warning message to users attempting to visit your site through search results or Chrome browser, alerting them that visiting this site could be harmful.
Unusual Admin Activity:
If you see any changes or updates in the backend of your website that you or your team did not make, it could mean that malware has allowed attackers to get into your administrative privileges.
Suspicious Files or Scripts:
Finding files or scripts on your server that you didn’t upload or that don’t belong to any of your web applications could mean that your server has been hacked and malware has been added.
Poor Search Engine Rankings:
Websites infected with malware often suffer from weakened SEO rankings because search engines penalize compromised sites to protect users.
Security Software Alerts:
Reliable security solutions might alert you about potential security breaches or suspicious activity indicating the presence of malware on your website.
Unexpected Communication from Web Hosting Provider:
If you receive communication regarding abnormal activity associated with your web hosting account (like exceeding bandwidth limits unexpectedly), it might signal the presence of malware leveraging your resources.
Understanding and recognizing these signs are crucial for any website owner as they form the first step toward mitigating and ultimately removing the threat posed by malware infections.
How to Remove Malware From Websites
Malware, can be inserted onto a website by modifying existing files or adding new ones. Since each hacking attempt is unique, it involves examining the website files to identify any suspicious elements. In this article, we will provide guidance to help you begin this process.
Pro Tip: Create a backup of your website before initiating malware removal. This precaution ensures that if any issues arise during the process, you’ll have a secure copy of all your files to fall back on.
How to Remove Malware from a CMS Like WordPress or Joomla
A malware infection on your website can be a nightmare, but don’t panic! Here’s a step-by-step guide to remove it from your Content Management System (CMS) like WordPress, Joomla, or others.
1. Gather Your Arsenal:
- Original Installation Files: These are your clean weapons against the malware. Download the version of your CMS that matches your current installation. Here are links for popular CMS platforms:
- WordPress: https://wordpress.org/download/
- Joomla: https://downloads.joomla.org/
- Drupal: https://www.drupal.org/download
- Prestashop: https://prestashop.com/prestashop-offers/classic/
- OpenCart: https://www.opencart.com/?route=cms/download
- Malware List: You might have received a list of infected files via email or found it in your hosting control panel. If not, contact your hosting provider’s support for assistance.
2. Identify and Quarantine the Infected:
- File Manager: Access your website’s file manager through your hosting control panel.
- Compare Files: Cross-reference the list of infected files with the actual files on your website. Here’s what to do for each scenario:
- Unfamiliar File: If a file on the list isn’t in the installation files or isn’t part of a known plugin or theme, it’s likely malware. Delete it!
- Infected Core File: If a core CMS file like
configuration.phporwp-config.phpis compromised, replace it with the clean version from the downloaded installation files. Remember to update your database login information after replacement. - Malicious Plugin/Extension: If the infected file belongs to a plugin, extension, or theme, delete it. You can reinstall a fresh copy later.
3. Clean Up and Secure:
- Replace or Delete: Once you’ve identified and handled each infected file, replace them with clean versions or delete them entirely.
- Update Everything: Now it’s crucial to update your CMS core installation, along with all plugins, themes, extensions, and any additional modules. This ensures outdated software with potential vulnerabilities doesn’t become a future security risk.
Bonus Tip (WordPress Users):
If you’re using WordPress, consider using a security plugin to scan for and remove malware in the future. Popular options include Sucuri Security and Wordfence Security.
Remember:
- Back up your website before making any significant changes.
- If you’re unsure about any steps, consult your hosting provider’s support team for assistance.
Remove Malware From Other Files
Sometimes, if your website is custom-made, you might need to get rid of the bad code that contains malware. Unless you know how to code, it can be hard to tell what is malware and what isn’t.
Look at the picture below to see an example.
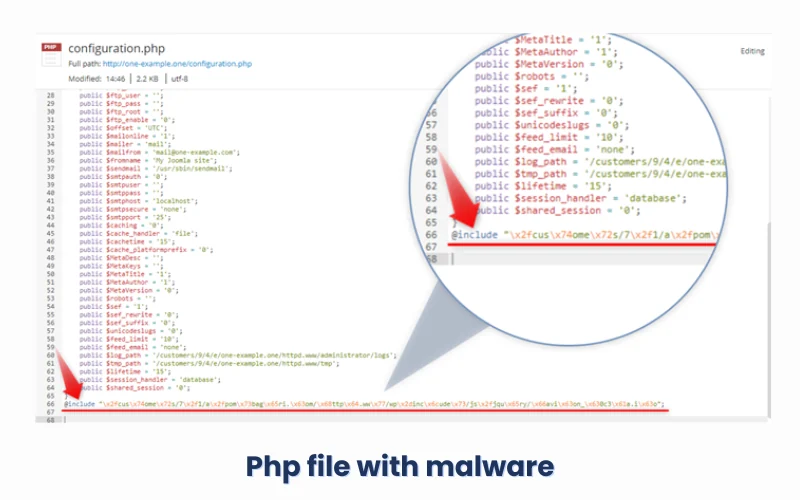
Usually, malware code is put at the beginning or the end of the file. Malware is often made up of long strings of text that look longer than the rest of the code in the file. We suggest editing the file in File Manager because it shows the code in different colors, which helps you see which part of the code doesn’t fit. Once you find the malware, delete it from the file and click Save in the top-left corner.
Remove Malware From Httpd.private or Tmp Folders
To remove malware from httpd.private or tmp folders, begin by accessing your website’s server files through a secure FTP connection or control panel.
Next, thoroughly scan these directories for any suspicious files or scripts. Identify and quarantine any detected malware-infected items, then proceed to delete or remove them from the server.
Exercise caution to avoid unintentionally removing critical system files. Finally, implement security measures to prevent future malware attacks, such as regular scanning, updating software, and strengthening access controls.
Articles You May Find Useful :
Website Maintenance Cost In 2024






